CYBER THREAT HUNTING
Don’t wait for your attackers to set off the alarms. Identify potential threats lurking in your systems before they disrupt your business.
- Home »
- Threat monitoring detection response »
- Cyber threat hunting
What is Cyber Threat Hunting?
Cyber threat hunting essentially involves proactively searching for threats that might have gotten through your organisations’ endpoint defenses. Typically information security systems will wait for an alert to start scanning systems and logs for a breach. However, threat hunting initiates a thorough search and sweep of your systems assuming that there is a breach, and in that process identifies potential issues even before there is an actual breach that could set off an alarm.
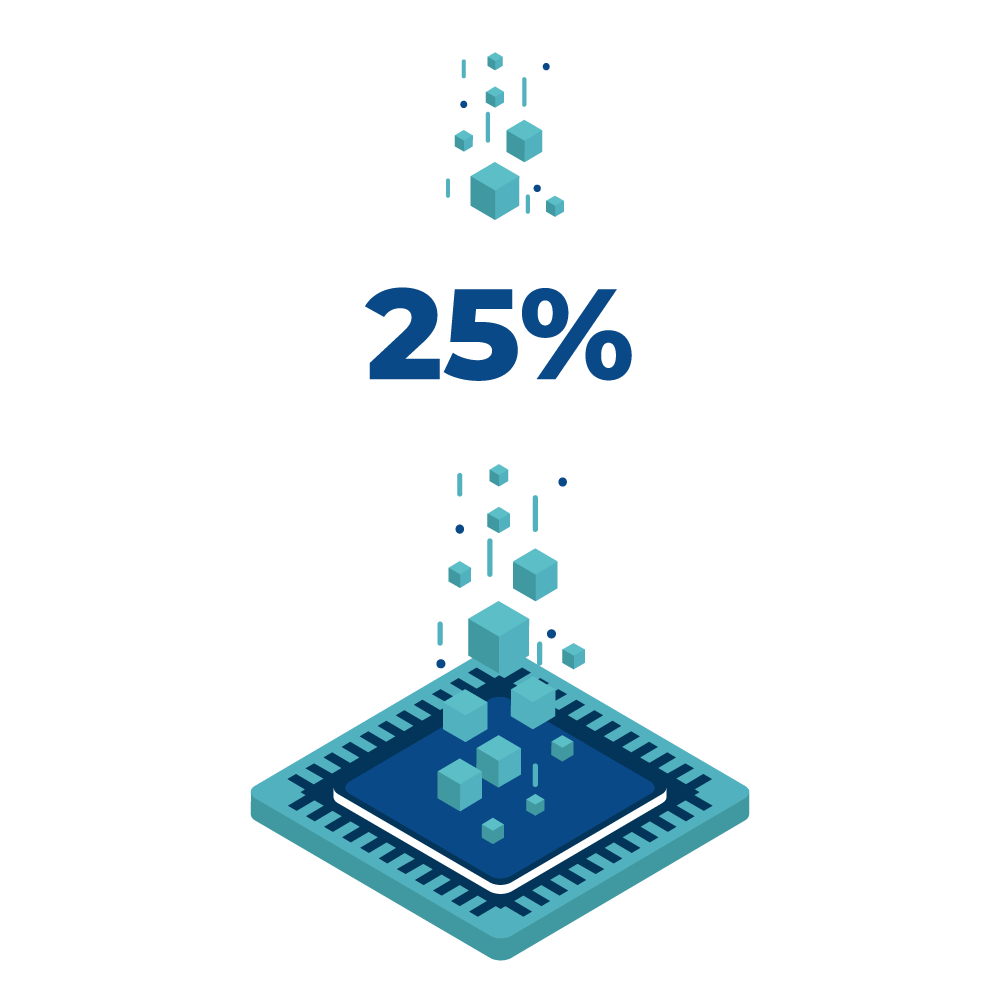
That’s the percentage of total cybersecurity breaches that go undetected for months.
Months within your organisation without your knowledge is enough time for a cyber criminal to cause serious damage to your business. Make sure that’s not the case for you, with proactive threat hunting.
Benefits of Cyber Threat Hunting
Uncover hidden threats
Proactively identify malware or any other threats that have managed to sneak into your network and systems. Threat hunting also does a great job of identifying and eliminating any malicious actors that may have gained access and are hiding in your networks and systems.
Reduce Investigation Time
The results and knowledge gained from threat hunting exercises can drastically reduce the investigation time for security teams when an actual security incident occurs. Threat hunting provides organisations with a better understanding of their security capabilities, systems and networks along with their vulnerabilities.
Faster Threat Response
Proactive threat hunting ensures that attackers cannot rely on the vulnerabilities present in a threat detection software to get the time to complete an attack. By actively looking for threats, your organisation is better equipped to respond quickly when anomalous activities are discovered.
Improve cyber defenses
Because threat hunting is carried out on the assumption that a potential threat has already occured or a malicious actor is already present within your networks or systems, it provides valuable insight into how to improve your organisation’s existing defenses.
Take Action Now!
Don’t get blindsided by surprise attacks. Proactively look for cyber threats and stop potential security breaches before they disrupt your business.
How We Do It: Cyber Threat Hunting Tools
StickmanCyber takes a thorough approach to systematically identify, document and respond to possible cyberthreats to your organisation:
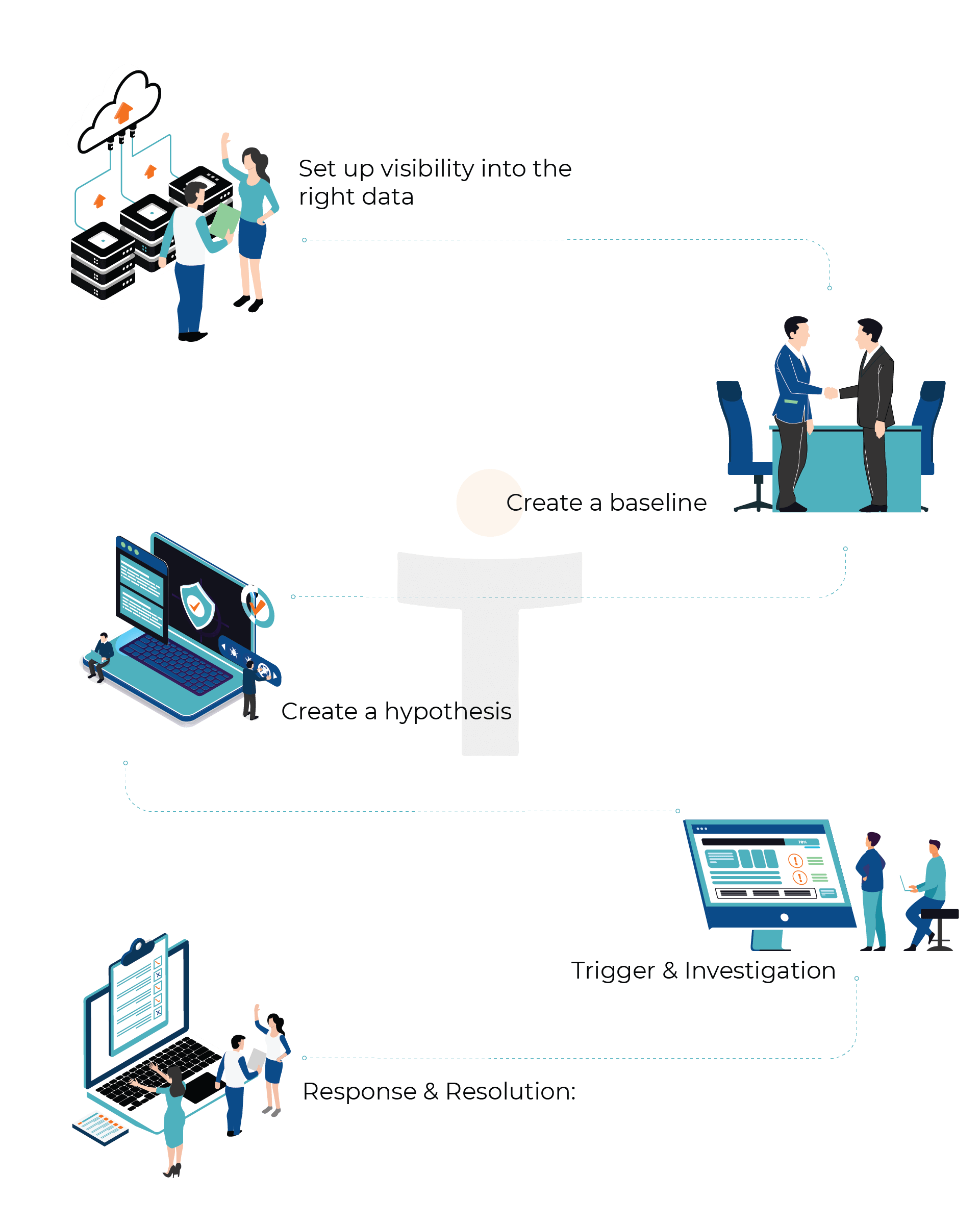
Set up visibility into the right data:
The first step is to ensure that the threat hunting team has visibility into a wide range of data - network activity, network traffic patterns, system events and logs, etc. Access to this data, along with the relevant context, creates an understanding of what to look for, what data sets to correlate in order to investigate potential threats.
Create a baseline:
We spend time in understanding your business and IT environment to create a baseline for what is normal user behaviour in your organisation. We also gain understanding of what data and information is of value within your organisation. This helps us spot and evaluate outliers from the normal, which could be potential threats.
Create a hypothesis:
Create different possible hypothetical threat scenarios, detailing an attacker's tactics, techniques and procedures to breach your defenses. We rely on several established attack frameworks, our team’s extensive and in-depth experience, and industry knowledge of the current threat landscape to create detailed and highly contextual hypotheses.
Trigger & Investigation:
Using the hypothesis as a trigger, our threat hunting team conducts an investigation in a specific area of the organisation. We use various tools and techniques to validate the hypothesis and look for a threat. If we do find evidence of malicious anomalies in a system or network, we dig deeper to uncover the source and the attacker.
Response & Resolution:
The final step of threat hunting is response and resolution. Using the results from the investigation, information security teams can work on responding to and mitigating any threats identified. The data collected from investigations can also be used to improve the technology used to identify threats, reducing overall human interaction, and further automating the process of threat detection.
Resources
Arm yourself with up-to-date information and insights into building a successful cybersecurity strategy, with blogs and webinars from the StickmanCyber team, and industry experts.
Top 10 Cybersecurity Uplift Focus Areas 2021
In this webinar, Ajay shares key insights, learnings and takeaways from the 100’s of projects run and executed by StickmanCyber’s and industry knowledge from the last 12 months culminating in the Top 10 investment focus areas organization’s need to have in place for 2021-2022 when it comes to improving and uplifting their cybersecurity posture.
Ready to Upgrade Your Cybersecurity Posture?
Know your exact challenge and want a solution partner? Just starting out on the cybersecurity journey? The StickmanCyber team can help.