Governance, Risk & Compliance (GRC)
Ever evolving, up-to-date cybersecurity to keep you a step ahead of the threats and hackers.
- Home »
- Cybersecurity grc governance risk compliance
What is Cybersecurity GRC (governance, risk and compliance)?
Cybersecurity threats today evolve at a rapid pace. How do you ensure your organisation is continuously secured? You do it with a thorough risk assessment of current and future business assets and processes. You do it by building resilient governance practices that can adapt and strengthen with evolving threats. And the StickmanCyber team is equipped to assist with all your cybersecurity GRC (governance, risk, and compliance) requirements.
-
What is a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is designed to get a detailed view of the possible cyber threats to your business, and your capabilities to manage the associated risks. The range of threats varies across businesses, so an in-depth risk assessment becomes the first and key step in understanding the gaps and vulnerabilities in your existing policies and procedures. Other than understanding your own risk profile, risk assessments can help in identifying third and fourth-party risk, which is a crucial part of the journey in getting secure.
Without a thorough risk assessment in place, your business might not discover where the challenges lie, and what aspects of cybersecurity to prioritise and invest in, to prevent disruption. Businesses are battling an extremely high rate of cyberattacks, across different industries. From malware and ransomware to phishing, to denial-of-service attacks; the threats out there are numerous. And any one of them can wreak havoc on your data, revenues, and reputation.
Why Conduct a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is crucial for both SMEs and large enterprises alike because:
Know the strength and weaknesses of your current security architecture and get the next steps to improve this first line of defense
Get a comprehensive risk profile of all your business assets and processes
Discover the high-vulnerability aspects of your business operations and move quickly to secure them
Identify any compliance gaps across your business processes for all major regulations like PCI DSS, ISO 27001, GDPR, NIST Cybersecurity Framework, and more
Get in-depth technical security assessments to detect malware, web apps and network security vulnerabilities, cloud security challenges and more

Vendor Risk Assessments help you understand your vendor risk profile and mitigate third and fourth-party risk rather than relying on incident response
What we deliver
StickmanCyber’s governance, risk and compliance (GRC) solution provides you with a comprehensive view of your current cybersecurity infrastructure, as against industry best practices. Know your next steps to close the gaps in your system. Our team works with you to:
- Understand your specific business context and cybersecurity requirements
- Identify existing gaps and vulnerabilities in your security posture
- Share a comprehensive list of recommendations to mitigate vulnerabilities and close security gaps
How We Do It
At StickmanCyber our team conducts risk assessments in five phases, as outlined below:
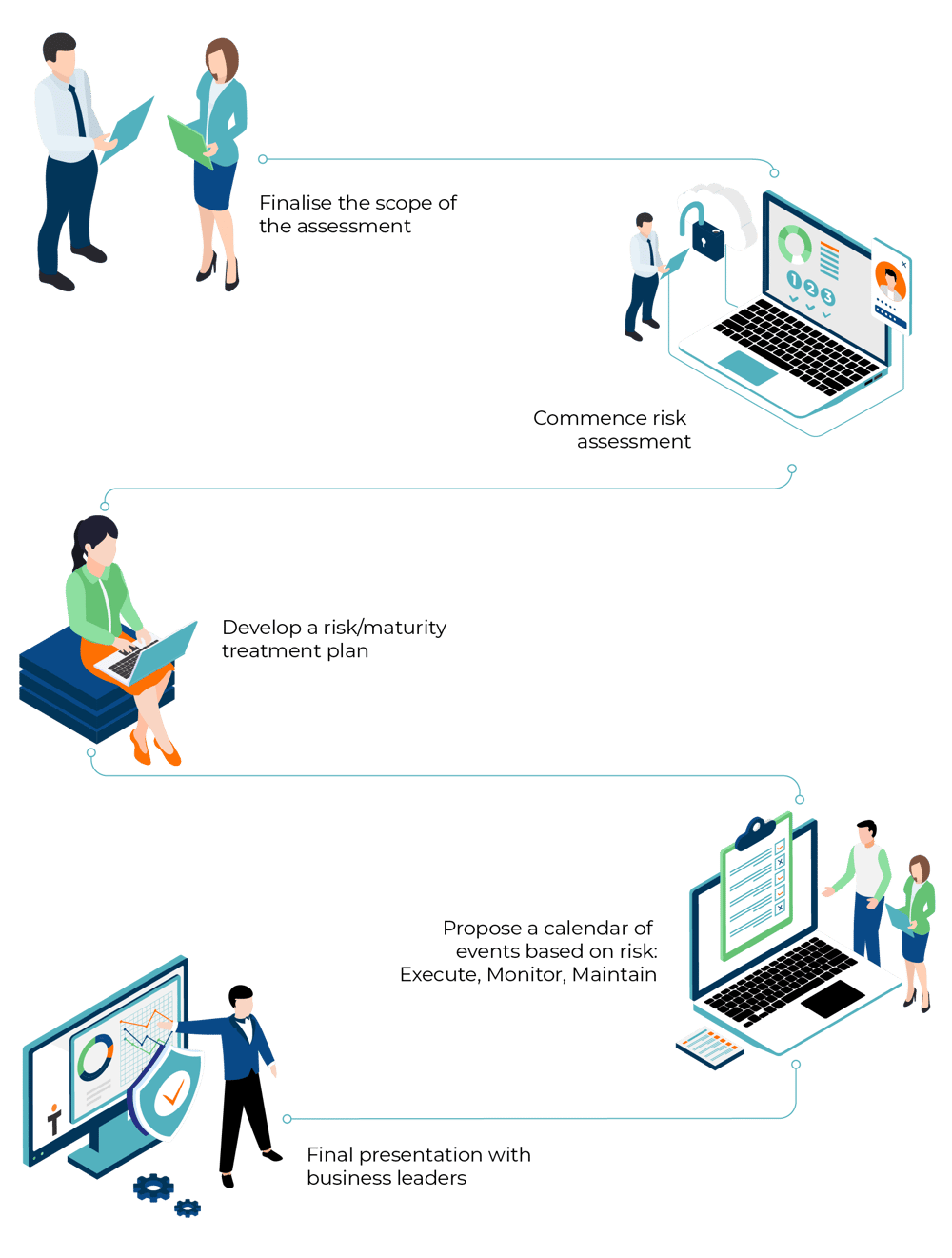
Phase 1 - Assess
- Finalize the scope of the assessment and context establishment workshop.
- Commence risk assessment:
-
- - Workshops and interviews to identify risk/maturity
- - Conduct a risk/maturity analysis on the scope.
- - Complete a qualitative risk/maturity evaluation.
- - Develop the risk/maturity assessment report.
Phase 2 - Plan
- Develop a risk/maturity treatment plan
- Propose a calendar of events based on risk/maturity criticality identified with estimates for:
- Phase 3-Execute
- Phase 4-Monitor
- Phase 5-Maintain
- Final presentation with business leaders and key stakeholders along with Q&A and next steps/actions for StickmanCyber-as-a-Service
Compliance and Certification
Compliance with industry-wide cybersecurity standards and certifications is an indication of trust for your customers. At StickmanCyber, we help you identify all the certifications and regulations your business needs to comply with. We can transform your systems to minimise risk, and get you compliant fast.
Get Aligned with Industry-wide Cybersecurity Standards
Cybersecurity frameworks, certifications, and regulatory compliance are often mandatory for doing business in certain industries. But more importantly, it is a signal to your customers and partners that your organisation is serious about security. It gives them assurance that their data and information is safe, and will be securely handled every time they do business with you. And building that trust is key to loyal business relations.

NIST Cybersecurity Framework
Develop a holistic approach to managing risk at your organisation with the NIST Cybersecurity Framework.

PCI DSS Compliance
Build trust with your customers and guarantee secure transactions with PCI DSS Compliance.

ISO 27001 Certification
Align with the gold standard of information security system management with ISO 27001 certification. Get your systems and processes compliant with StickmanCyber.

APRA 234 Assessment
Are you a financial institution or an insurance firm? StickmanCyber can help review your current cybersecurity framework against the requirements of APRA 234, identify compliance issues, and provide recommendations for remediation.

ISM by Australian Signals Directorate
ISM is designed to help government agencies to apply a risk-based approach to protecting their information and ICT systems. Review your current systems and get compliant with StickmanCyber.

Australian Privacy Principles
Align with the new Australian Privacy Principles to avoid privacy breaches, massive financial consequences and reputation destruction.
Get an in-depth view of the range of cyber threats out there
We put together a compilation of:
- The major cyberattacks in Australia last year, across healthcare, financial services, technology, and e-commerce
- How they impacted the businesses
- How they could have been prevented
.png)
FAQ
What is Cybersecurity GRC?
Cybersecurity Governance, Risk and Compliance (GRC) is a framework that helps organizations manage and mitigate cyber risks while maintaining compliance with industry regulations and standards. It involves implementing policies and procedures to govern cybersecurity, identifying and assessing risks, and ensuring compliance with relevant laws and regulations.
What cybersecurity GRC services does your company offer?
Our company offers a wide range of Cybersecurity GRC services, including:
- Governance services: such as developing and implementing cybersecurity policies and procedures, incident management, and compliance management.
- Risk management services: such as identifying and assessing cyber risks, vulnerability assessments, threat intelligence, and penetration testing.
- Compliance management services: such as HIPAA, SOC 2, PCI-DSS and other regulatory compliance assessments, reporting and certification.
How is Stickman Cyber different from other cybersecurity GRC companies in Australia?
Our company differentiates itself by offering a comprehensive and customized approach to Cybersecurity GRC. We have a team of experienced security professionals who stay up-to-date with the latest threats, best practices, and regulations. Additionally, we use advanced security technologies and tools to provide real-time monitoring and protection for our clients. We also offer a customized approach to GRC, tailored to the specific needs and regulations of each client.
How does Stickman Cyber help me with compliance?
Our company can help you comply with industry regulations such as HIPAA, PCI-DSS, SOC 2, and others by providing assessments, monitoring and reporting to ensure that your organization is following the necessary security controls and protocols. Additionally, our team of security experts can provide guidance and support in developing and implementing policies and procedures to meet compliance requirements. We also provide regular compliance reporting and certification as per the client's requirement.
How does your company help me manage cyber risks?
Our company helps you manage cyber risks by identifying and assessing potential risks to your organization, and implementing controls to mitigate those risks. We also provide regular security assessments and penetration testing to identify vulnerabilities in your network and applications. Our team of experts will also provide guidance on threat intelligence and incident management to help you respond quickly and effectively to potential threats.
How much does your cybersecurity GRC services cost?
The cost of our Cybersecurity GRC service varies depending on the specific needs of the client. We offer customized packages to meet the unique requirements of each client and can provide a quote after evaluating your organization's security needs.
How do I get started with your cybersecurity GRC service?
To get started with our Cybersecurity GRC service, please contact us to schedule a consultation with one of our security experts. During the consultation, we will discuss your organization's specific needs and objectives and provide you with a proposal and quote for our services.
Resources
Arm yourself with up-to-date information and insights into building a successful cybersecurity strategy, with blogs and webinars from the StickmanCyber team, and industry experts.
Creating a Cybersecurity Strategy for your Organisation
Throughout the webinar, Ajay Unni, CEO & Founder at StickmanCyber, uses a number of real-world examples to highlight the strategies that work (and why), the most common mistakes organisations make when designing and building a strategy and the pitfalls of implementation without the right internal backing.
Ready to Improve and Enhance Your Cybersecurity Posture?
Know your exact challenge and want a solution partner? Just starting to evaluate your cybersecurity GRC requirements? The StickmanCyber team can help.

