CYBER SECURITY INCIDENT RESPONSE PLAN
Are you prepared to quickly and effectively respond to a cyberattack? Do you have a plan in place to ensure the safety of sensitive business assets, and minimise damage, disruption, and data loss?
- Home »
- Threat monitoring detection response »
- Incident response
What is Incident Response?
Incident Response refers to the processes and policies an organisation uses to respond to a cyber incident such as an attack or data breach. The goal of Incident Response is to mitigate the damage of an attack i.e. reduce the recovery time, effort, costs and reputational damage associated with a cyberattack or data breach. It is also meant to investigate and understand the cyberattack and gather insights that help prepare for and prevent similar attacks in the future.
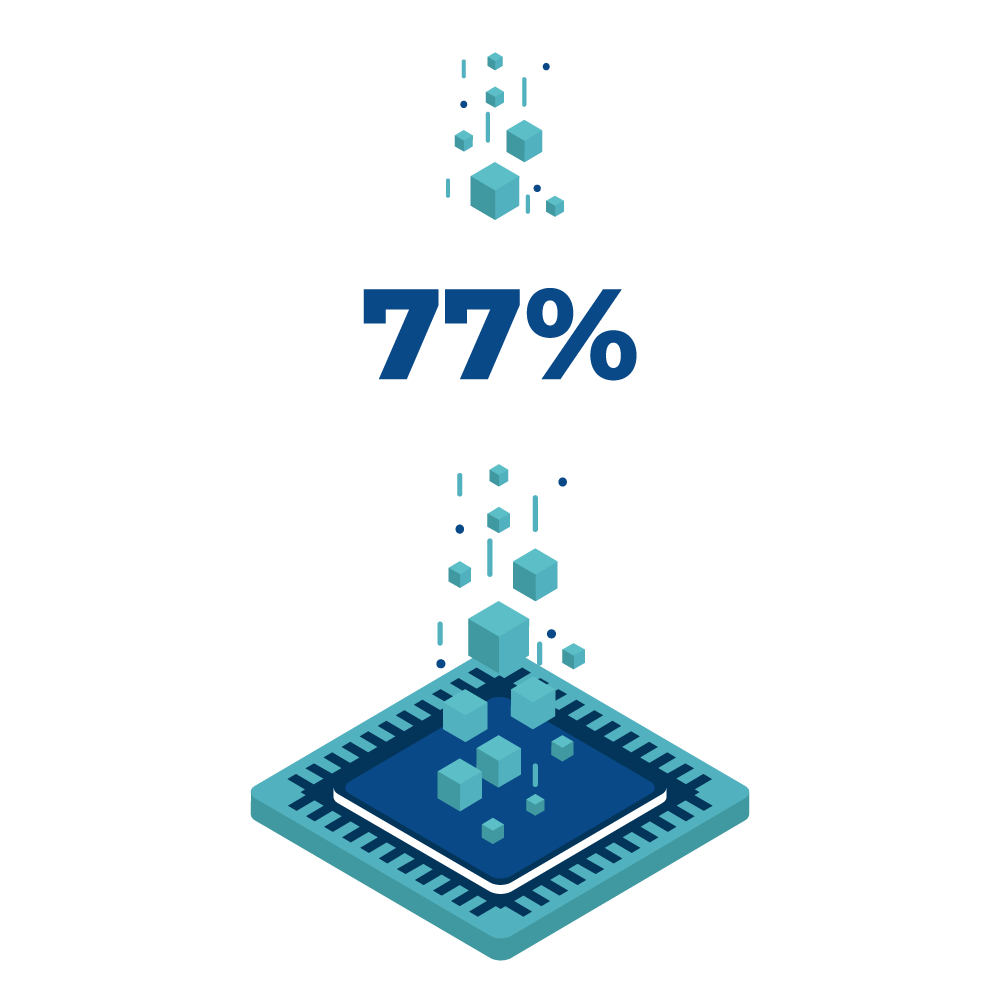
That’s the share of organisations that DO NOT have a cybersecurity incident response plan
And you don’t want to be among the companies that are unprepared for cyberattacks.
Post a security breach, every second counts. So make sure you have a detailed, and repeatable incident response plan.
Why Incident Response is Crucial?
Incident Response is essentially a thorough plan of action for what your organisation is supposed to do in the event of a cyberattack. It’s important because:
- Trying to put together a response plan after a cyberattack is as good as not taking any action at all. Every second of inaction means greater havoc on your systems, more disruption, and loss of customer trust. The Incident Response plan allows you to get into action right away, and keep the damage to a minimum.
- The lack of a well-designed Incident Response plan can also trigger greater government regulation in the aftermath of a cyberattack, as it paints a picture that your organisation is unable to handle a scenario like this.
Take Action Now!
Leverage every past and potential cyber threat to further bolster your defenses. Speak to our experts and identify the right cybersecurity solution for your business.
How We Do It?
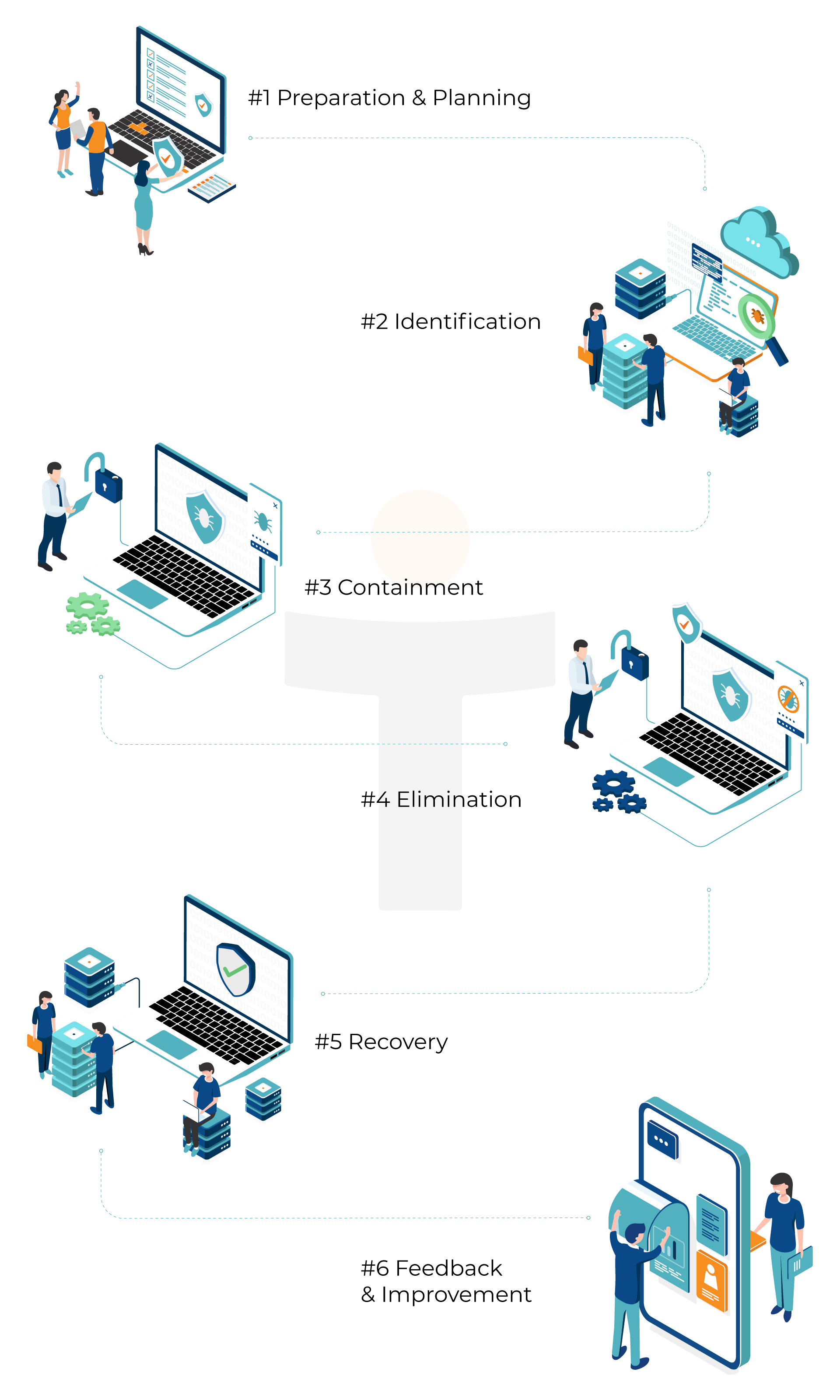
At StickmanCyber, we follow the six key steps for incident response:
#1 Preparation & Planning: Evaluate the effectiveness of your existing security measures and policies - identifying vulnerabilities via assessments or scans which help in prioritising which type of incidents need to be responded to as soon as they are identified. All of this will lead to the creation of an incident response plan.
#2 Identification: Identify the presence of any suspicious activity within your organisation. Once found, conduct and document a detailed analysis of its origin, type, as well as goals of the attackers. This information is communicated to stakeholders, authorities, and legal counsel, instructing them on the steps that need to be taken now that a cyber incident has occurred.
#3 Containment: We prioritise getting to the containment stage as quickly as possible so that repercussions of the attack can be controlled and mitigated. As a short-term measure, we focus on isolating immediate threats. Long-term containment measures involve re-assigning access controls to unaffected areas to lower the chance of the attack spreading across the infrastructure.
#4 Elimination: Once the threat has been contained, our team begins ejecting attackers and eliminating malware from systems. This phase continues until all traces of the attack are removed.
#5 Recovery: At this stage, we bring the patched and updated replacement systems online. The recovery phase also involves security teams monitoring networks and systems for a period after the attack to make sure malicious actors don’t return.
#6 Feedback & Improvement: Finally, we review with you how effective the incident response was and what can be done better next time. This stage also involves security teams completing thorough documentation of events for later review or reference.
Resources
Arm yourself with up-to-date information and insights into building a successful cybersecurity strategy, with blogs and webinars from the StickmanCyber team, and industry experts.
Strategies to mitigate cyber security incidents
Throughout the webinar, Ajay Unni, CEO & Founder at StickmanCyber, uses a number of real-world examples to highlight the strategies that work (and why), the most common mistakes organisations make when designing and building a strategy and the pitfalls of implementation without the right internal backing.
Ready to Upgrade Your Cybersecurity Posture?
Know your exact challenge and want a solution partner? Just starting out on the cybersecurity journey? The StickmanCyber team can help.