With the increasing popularity of the web and mobile applications, organisations and businesses are now adopting them as useful tools to stay connected with their customers. But with the increased reliance on these modern tools, the probability of malicious attacks on organisational networks and applications has also increased considerably.
Hackers use security flaws in applications to steal confidential customer information which can eventually lead to heavy losses for the organisation. According to recent research, three out of four websites are prone to attacks and most of the attacks are on applications, which cannot be protected by SSL or firewalls alone.
It is here where the concept of penetration testing (‘Pen Test’) comes into the picture.
Simply put, penetration testing is a procedure for testing the security of a system or software application by making a deliberate attempt to compromise its security. It tests how vulnerable underlying network configurations and operating systems are. This helps to prepare for any possible malicious attacks or avoid the potential breach of data at the hands of an outside party.
How Can Penetration Testing Help You?
Here are some of the reasons why you should consider regular penetration testing for your organisation, and in particular, to make it a part of your software development lifecycle (SDLC). You should use regular penetration testing:
1. To outsmart automated hacking tools: Lists of vulnerabilities that can be exploited can now be easily obtained online. The use of automatic hacking tools has made it much easier for even amateur hackers to carry out successful attacks and gain access to confidential data.
2. To detect and fix vulnerabilities on time: Vulnerabilities will always exist, no matter how secure your systems are. It’s therefore smart to conduct regular penetration tests to detect all potential vulnerabilities and fix them before a malicious user does so. This proactive approach will help organisations avoid any threat of confidential information being leaked as a result of a breach of data.
3. To detect any breach of data that may have already existed: Not only will a penetration test help find vulnerabilities, it will also help reveal any loss of private information that you may have already incurred and which otherwise may not have been revealed for a long time.
4. To help determine other weaknesses: Penetration testing can find other weaknesses such as hardware and software loopholes, and weaknesses in employee security awareness and system usage.
5. To help practice ongoing security: This enables organisations to build more confidence in terms of secure information systems. As new threats emerge with every passing day, regular penetration testing allows you to stay up to date and counter any conniving attacks.
6. To detect any weak practices within your organisation: Internal penetration tests can help organisations find out whether or not their policies and procedures are up to date, understood, and followed by employees. It can also reveal other weaknesses such as ineffective password protection procedures, patching policies, and data encryption techniques.
7. To help measure the performance of your network and systems and take preventive or corrective actions accordingly.
8. To prepare for bad times: In case your data does get compromised for real as a result of an attack, your penetration testers and information security personnel will have gained enough experience to deal with the incident and will be better able to respond to the attack.
9. To document your security practices: Penetration testing reports provide written evidence to the management about where your organisation stands in terms of its information security. Documented reports also provide you with a justification of the costs incurred on acquiring the right technology to stay more secure.
10. To conform to penetration testing requirements such as PCI Data Security Standards and ISO 27001.
11. To provide assurance to customers that their data is safe and protected at all times.
12. To reduce costs in the long run: Conducting regular penetration tests, especially during the software development lifecycle, reduces costs in the long run by reducing the number of vulnerabilities.
Why Should You Make Penetration Testing a Part of the SDLC?
Making penetration testing an integral part of your software development lifecycle ensures that the end product turns out to be safe and secure for your customers. What normally happens is that a product is first developed and then at the end, a security assessment is conducted to check for vulnerabilities. The issues are usually fixed with patching software, but this turns out to be much more costly than addressing the real issue.
If issues are fixed during the software development process, much of the costs can be reduced by avoiding multiple cycles of testing–patching–retesting the software at the end. Ever since the threat landscape has changed, organisations are now looking forward to providing more secure applications that are able to sustain their profitability and attractiveness for the customer.
As information security is getting more fragile at the hands of malicious attackers found everywhere on the internet, measures to counter such attacks also need to be improved. Malicious hackers look for all the routes to enter into the network and one of these routes is the application host. Hence, the applications hosted by your organisation must not be vulnerable, or else information can be easily compromised. Employing a team of penetration testers during the SDLC phase helps avoid the costs that may result otherwise from breaches of data.
Below is a generic diagram of how our penetration testing program for SDLC works.
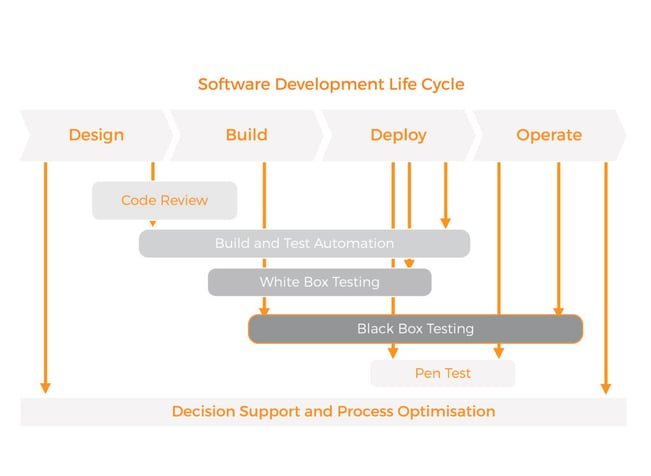
It’s important to keep in mind that penetration testing goes far beyond a set of automated tools. It is a broad approach, and a whole process that involves the use of appropriate tools as well as human knowledge and expertise. A successful penetration tester needs to have vast experience, a sharp intuitive mind, and an ability to critically analyse situations. This unique blend of abilities is necessary to allow a penetration tester to carry out successful testing of vulnerabilities. This is something that automated tools alone cannot achieve.
The process of application security starts right after you begin the development process. It is, therefore, better to understand the process by dividing your SDLC into phases and addressing each phase differently.
- Design – In this phase, you make a secure design process and review, along with formal methods like specification and modelling languages.
- Build – Developing code that can be tested and used for automated review and inspection later.
- Deployment and Execution – Inspecting the executed application. When conducting automated reviews and inspecting applications, use static (white box) testing and dynamic (black box) testing respectively.
Once the product is complete and ready to be launched, it is recommended to carry out a final penetration test before the product goes for the user acceptance test, to make sure that the test version is safe and readily accepted by consumers.
Regular penetration testing is definitely something we can help you with. Here’s more information on Stickman Consulting’s penetration testing services.
And if you’d just like to know more, or need clarification of any sort, contact us here with any questions.