Our Information Security Advisories have helped countless Australian businesses stay secure, and now we're bringing them straight to your social media feed.
Executive Summary
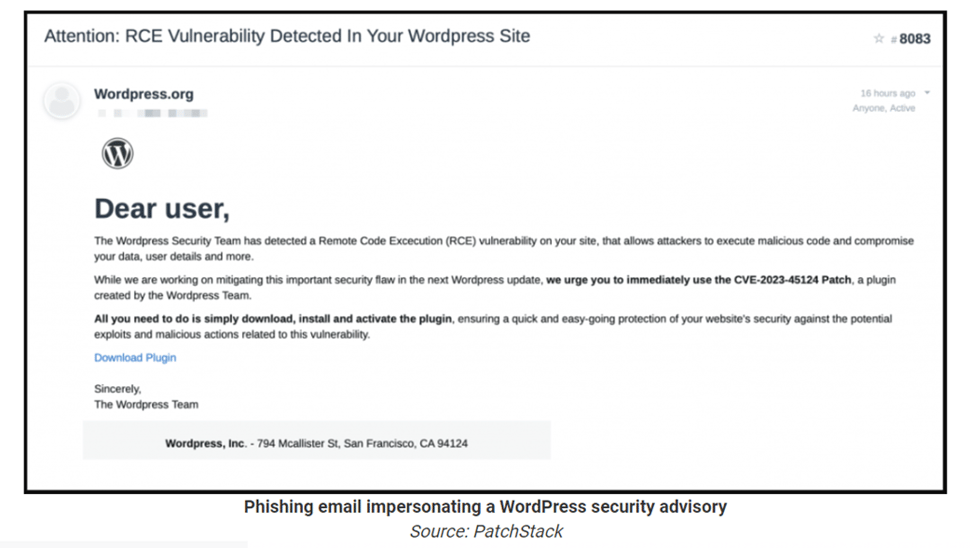
A phishing campaign has been identified targeting WordPress users, spreading fake WordPress security advisories regarding a non-existent vulnerability, CVE-2023-45124.
The attackers use deceptive emails, posing as WordPress, to trick administrators into downloading and installing a malicious plugin. Once installed, the plugin creates a hidden admin user and establishes a backdoor, enabling potential unauthorized access and control over affected WordPress sites.
Systems Affected
WordPress sites are vulnerable to this phishing campaign. Users who fall victim to the deceptive emails and subsequently download and install the malicious plugin are at risk.
.png?width=1041&height=552&name=image%20(1).png)
Risk
The risk associated with this campaign is significant. Attackers gain unauthorized access and control over compromised WordPress sites, potentially leading to various malicious activities. The backdoor functionality includes file management, a SQL client, a PHP console, and a command line terminal, providing attackers with a range of capabilities.
The true operational goal of the backdoor remains unknown, but potential activities could include injecting ads, redirecting visitors, stealing sensitive information, or even blackmailing site owners.
Recommendations
- Avoid Clicking Suspicious Links:Exercise caution when receiving unexpected emails, especially those claiming urgent security issues. Do not click on links in emails that seem suspicious or request immediate action.
- Verify Official Communications:Verify the authenticity of emails claiming to be from WordPress or any other platform. Legitimate organizations usually communicate through official channels, and security advisories are typically posted on official websites.
- Scan for Indicators of Compromise (IoCs): Check for the presence of the malicious plugin by scanning for indicators of compromise (IoCs), including the 'wp-autoload.php' file with a SHA-256 hash of ffd5b0344123a984d27c4aa624215fa6452c3849522803b2bc3a6ee0bcb23809 , the 'wpress-security-wordpress' plugin, and the hidden admin user 'wpsecuritypatch.'
- The following malicious domains:
- en-gb-wordpress[.]org
- wpgate[.]zip
- Educate Users:Educate WordPress site administrators and users about phishing threats and the importance of verifying the authenticity of emails before taking any actions.
References